10.70.122.5589: System Address Analysis
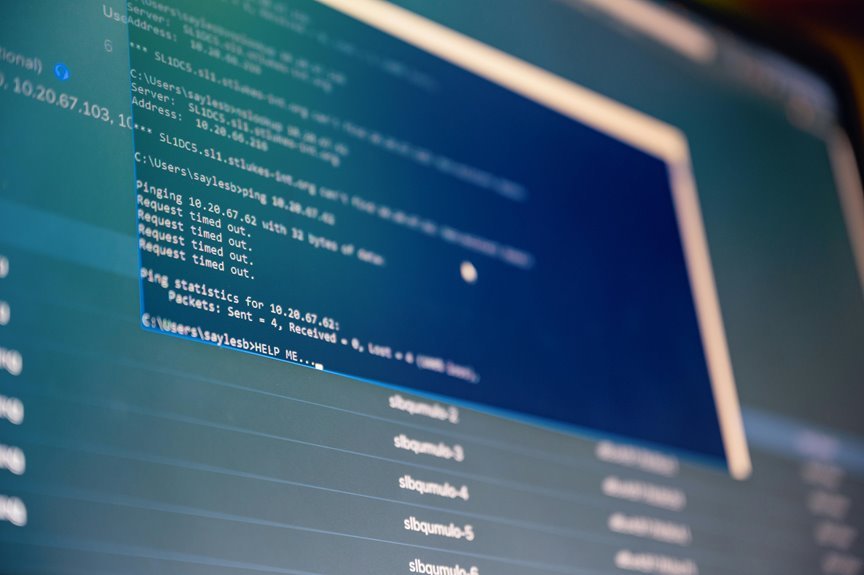
The address 10.70.122.5589 serves as a case study in system address analysis. Its structure highlights the significance of adhering to established conventions in IP addressing. Notably, the final octet exceeds the valid range, raising questions about the implications for network functionality. This discrepancy may impact communication protocols and security measures. An examination of such errors can reveal vulnerabilities, prompting a closer look at best practices in address management.
Understanding System Addresses
System addresses serve as critical identifiers within computing environments, enabling the organization and retrieval of data across various components.
Effective system identification relies on precise address allocation, facilitating seamless communication and resource management.
Analyzing the Structure of 10.70.122.5589
The structure of the address 10.70.122.5589 highlights significant aspects of addressing conventions in networking.
This address exemplifies standard address formatting, where each segment represents distinct data representation categories.
The four octets, ranging from 0 to 255, demonstrate the binary encoding utilized in networking.
Such structuring facilitates efficient communication, ensuring clarity while allowing for a vast array of addressable devices within the network.
Implications for Network Management and Security
How can the structure of network addresses influence management practices and security protocols?
Analyzing address configurations reveals potential network vulnerabilities, guiding administrators in implementing effective traffic monitoring solutions.
By understanding address hierarchies and patterns, organizations can enhance their security frameworks, enabling proactive measures against threats.
This insight fosters a robust management strategy, ensuring both operational efficiency and resilience in an increasingly complex digital landscape.
Conclusion
In conclusion, while 10.70.122.5589 boldly flaunts its audacity with an outlandish octet, it serves as a cautionary tale for the networking elite. This whimsical address, a true rebel against the confines of numerical norms, illustrates the absurdity of neglecting foundational principles in system architecture. As networks race toward the future, may we remember that even the most spirited addresses must adhere to the mundane realities of binary limits—lest we find ourselves lost in a digital circus.